Cryptograhy Blog
As the blog's name suggesting, Cryptography is an encryption or decryption of data over the internet/ local server. Cryptography is a big part in networking and security. So, the question is, "did it also important for CTF?" The answer is YES. Cryptography is also play a very important role in CTFs as they have seperate question type in CTF.

What is Cryptograhy?
As I explained above, Cryptography is an encryption or decryption of data over a network. Let me explain the mechanism of cryptography -
Taking a example of whatsapp, when you (means client) send a message to your friend (means another client). Firstly, message get encoded by using some algorithms and then pass over the whatsapp's network with your IP address and encrypted message and some more little information which are required. When the message is received by your friend, the message then decrypted and show the message on whatsapp with your number.
This is an example that how cryptography works. NOTE - if someone get your encrypted message using spoofing or packet capturing, then he/she can also decode the message using the algorithm use by whatsapp. Well for your information, whatsapp using Curve25519 algorithm for encrptyion. How i know this? Salute to google search.
Types of Cryptograhy
Cryptograhy is mainly divided in three types -
- Symmetric Key Cryptography - In this type of cryptography, Sender and reciever have a same key for encryption or decryption of data. The key is kind of password through which it is encrpyted or decrpyted. So , the key over the encrpytion is same on both side. Some examples are RC4, AES, DES, etc.
- Hashing Cryptography - Hashing is a method of cryptography that converts any form of data into a unique string of text. Any piece of data can be hashed, no matter its size, type, length, the hash that any data produces is always of same length. Hashing techniques are very common these days for encrpytion of data even whatsapp, email, and many other companies using it. Some examples are MD5, #SHA-1, #SHA-256, #SHA-512, etc. Hashing is also used in Cryptocurrency.
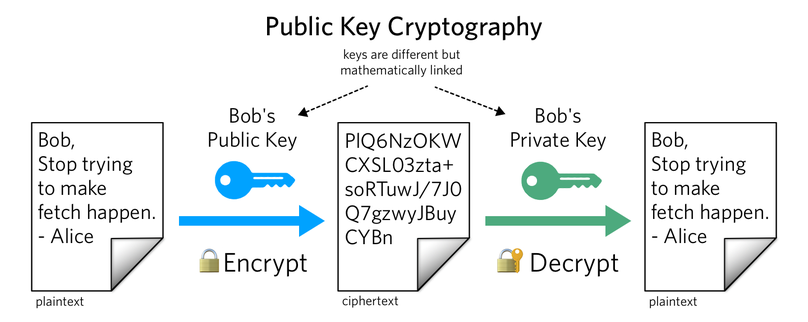
- Asymmetric Key Cryptography - Asymmetric Cryptography is also known as public key cryptography. In this method, there are two keys for encrpytion and decrpytion. The data is encypted with some key and decrpyted using some other key. That's why, This algorithm is better then symmetric algorithm but its speed of encrpytion and decrpytion is slow then symmetric algorithm.
Tools For Cryptography
There are many tools for cryptography in kali linux or on internet for use in CTF -
- John the ripper toolkit
- Hydra toolkit
- hashcat tool
- Johnny (GUI interface of John the ripper)
There are many other tools but I think this much is sufficient.
References
I think the above introduction of cryptography is sufficient for your understanding. I am also providing some links regarding cryptography for better understanding through writeups.
References:- ROT-i : Writeup by DownUnderCTF
- Extra Cool Block Chaining : Writeup by DownUnderCTF
- Flags : Writeup by kevinjycui
Final Words
Cryptography is not a small topic. If you go in depth, you find that cryptography is basically involve in everything and in every question.
